Security Is Not a VPN Problem
Go ahead and use your hotel WiFi
In this post, I:
Quickly define what a virtual private network (VPN) is and what it actually protects you from
How VPNs used to be fundamental security tools a decade ago before we had HTTPS everywhere
How VPNs no longer solve security problems now that HTTPS is everywhere, especially for regular people (and regular companies)
VPNs
We've talked a lot recently about controls that we keep around, not because they provide any value, but because we haven't really adjusted to the technical changes of the past 10 years. We haven't thought about why we have them, and just act like monkeys in a cage.
A prevalent one is virtual private networks (VPNs). VPNs are software that allows you to remotely connect to a separate, often private, network over an encrypted connection over TLS (Transport Layer Security). You connect to a VPN server, which then routes your requests, either internally within the organization's network or onto the wider internet. An observer of your connection (e.g., a compromised router, Starbucks WiFi, etc.) can only see your encrypted messages to the VPN server.
Historically, CISOs, security thinkers, Cisco sales reps, and YouTube channels have argued that VPN is a critical element of any corporate (or personal) security posture. The idea is that if you are on an "untrusted" network (Starbucks WiFi, say), you should use a VPN to protect all of your traffic. Otherwise, you risk something horrible happening to your connections to sites like your email and your bank.

NOTE: For the rest of this post, I am talking about VPNs in the sense of protecting you from someone snooping on or modifying your communications over the internet, especially on untrusted networks or WiFi. I’m not talking about it as a tool for connection to your work network or cloud infrastructure remotely, or any of the network inspection services they may provide.
Speaking of encrypted connections, HTTPS (Hypertext Transfer Protocol Secure, the words are not important1) is a standard that applies TLS encryption directly to your connection to websites. When you see that https:// in the browser, it means that your connection to that website is encrypted, and no one sitting between you and Amazon or Facebook or whatever can view your traffic or pretend to be the site you’re connecting to.
For a while, the internet community was bad at using HTTPS. After much hell-raising, that’s not true, and HTTPS has been basically everywhere for over a decade now. Encrypting your connections is the primary point of a VPN, and HTTPS does that at the site connection level, so why all this VPN pushing?
A VPN provides the following protections above and beyond HTTPS:
The IPs of servers you connect to
The size of the requests you send. This is rarely important but occasionally leads to a fun side channel.
It used to hide your DNS queries, though DNS over HTTPS has been the default in Chrome since 2020, so this also is no longer a real VPN advantage
That's it! I've heard people argue that a VPN provides defense in depth from misconfigurations in HTTPS or TLS. This argument used to have merit a decade ago, but now we have browsers that validate this stuff for us very well; this is why Chrome is always yelling at you about websites. We also have most load balancers, edge firewalls, and CDNs to ensure secure connections with a checkbox. It's hard to misconfigure something like this:
Disclosing DNS requests and the IPs of the servers you connect to is a mild privacy problem. If you're a political dissident, a journalist, a politician, or someone into really kinky pornography (these are not mutually exclusive categories), then the privacy guarantees of a VPN are valuable. (Suggestion: Please don't watch really kinky porn things on your corporate VPN, or Starbucks WiFi for that matter).
These privacy concerns are very real for some people, but not really a thing for most modern companies with a SaaS-based corporate IT stack, or an individual user trying to remain secure. Sans VPN, we're disclosing at most DNS queries and the IPs of servers we're connecting to. There are probably much easier ways to figure out that a sales rep uses Google, Zoom, Slack, and Salesforce? Or that a random individual goes on TikTok too much and banks with Chase? This is further minimized as many applications front all of their connections with common edge security providers and CDNs; going to several sites will end up just connecting to the same Cloudflare or AWS IP, masking the service you’re connecting to.
Before you mention the traffic monitoring, DNS filtering, or in-flight malware prevention power of some corporate VPNs, sure. That's a bit out of scope here, since those are useful for all traffic, not just being on a Starbucks access point. Same with connecting to corporate infrastructure. There are also other solutions to these problems than a VPN.
VPNs are great for piracy, though.
Note: I have considered that in order for it to be safe for dissidents and journalists to use VPNs, VPNs needed to have a widespread, non-dissident use case. Perhaps a group of enterprise CISOs and VPN vendors decided that in pure selflessness, they would buy and promote a useless security tool in mass, just to give those dissidents cover. If that's the case, my bad! For the low price of giving me an invite to your security Illuminati, I'll happily take down this blog post.
This limited protection isn't something that a security organization with limited resources should invest in. It's certainly not something we should suggest ordinary people, with a limited capacity to care about their security, should focus on. We have a very limited number of fucks we can get our relatives to care about, and it’s damaging to have people use one (and their hard-earned cash) on something that provides no value.
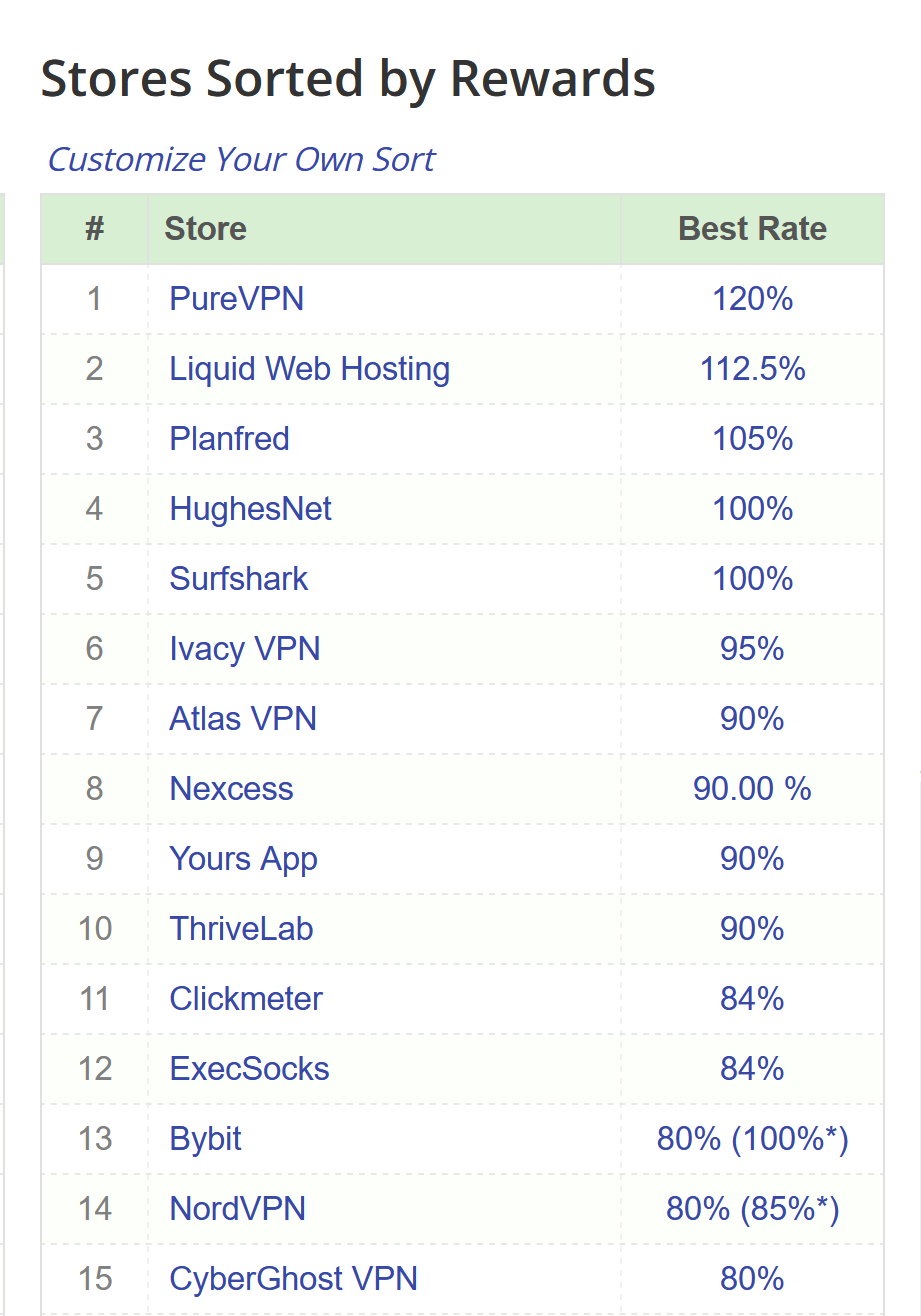
As a last piece of evidence, if you look on cashbackmonitor.com, you'll regularly see that many of the top cashback-providing sites are usually consumer VPN sellers:
In addition to the obvious ones, Surfshark is also a VPN provider, giving us 6/15 of the top cashback returns from VPN companies. Whatever a PureVPN is will pay you to use their product! That's not usually a sign of a high-value tool, and probably not of one that’s trustworthy. If they’re paying you to use the product, someone else is probably paying them for your data.2
I'd Love To Hear From You
Do you agree? Are there even sillier things we love too much? Disagree? Intensely? Are VPNs your favorite thing? Do you have any other feedback for me? Please leave a comment below; I'd love to hear it!
The actual words in the acronym are so unimportant that HTTPS is the only Wikipedia link I’ve ever seen to just the acronym and not the spelled-out concept.
I’ve heard the conspiracy before that many VPN providers are just government sting operations, where they condition everyone to use them when doing illicit things, and then run all of the VPN providers to catch you doing those illicit things. The FBI can certainly fund you using PureVPN at 120% cashback


VPNs are a false sense of security, zero trust all the way